See FSProtect in Action
Threat Centric Features
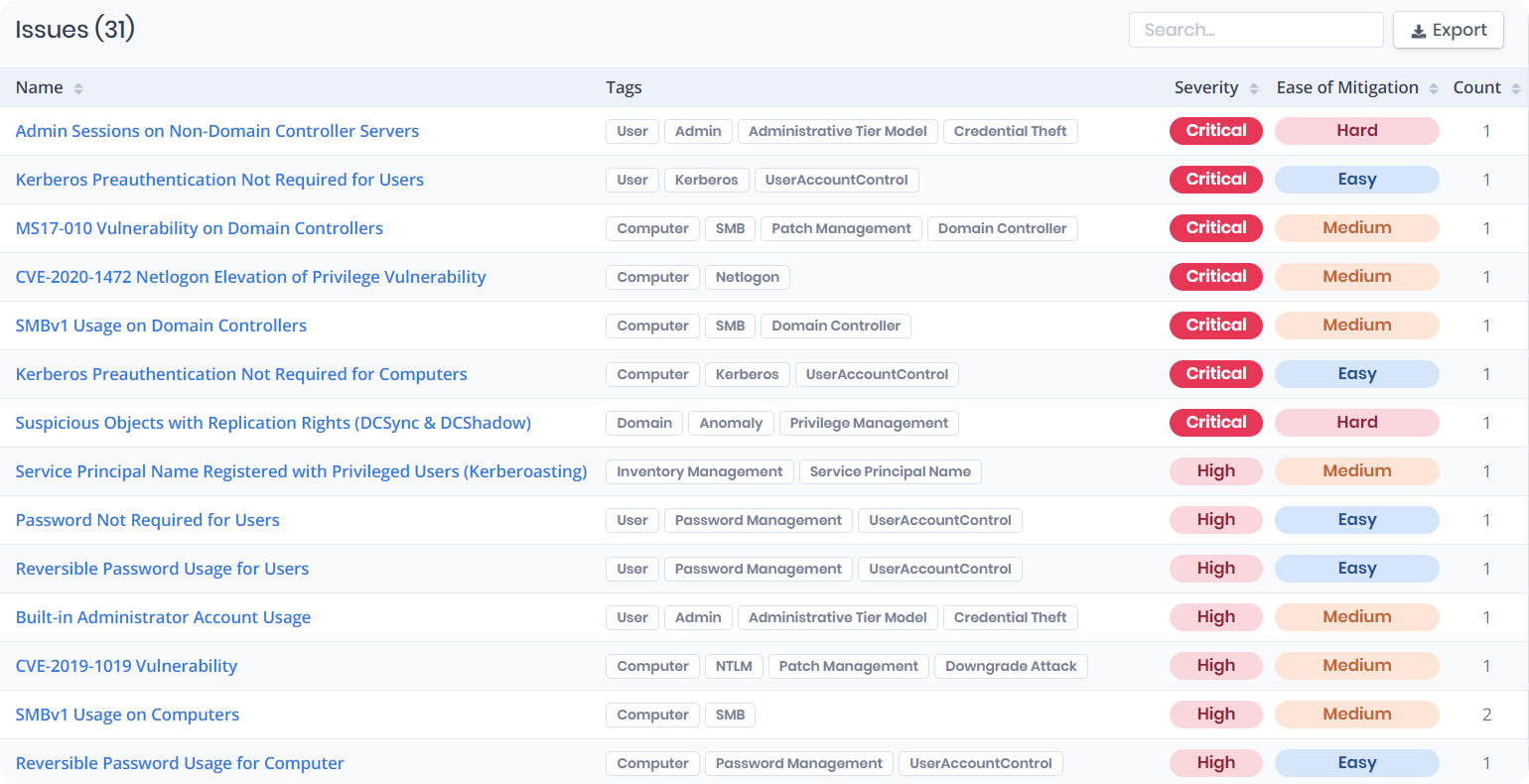
Advanced threat actors take advantage of Active Directory deficiencies most of the time. FSProtect, aims to restrict the adversary maneuverability by detecting vulnerabilities misconfigurations, and hidden attack paths lurking in the complex relationships with minutes.
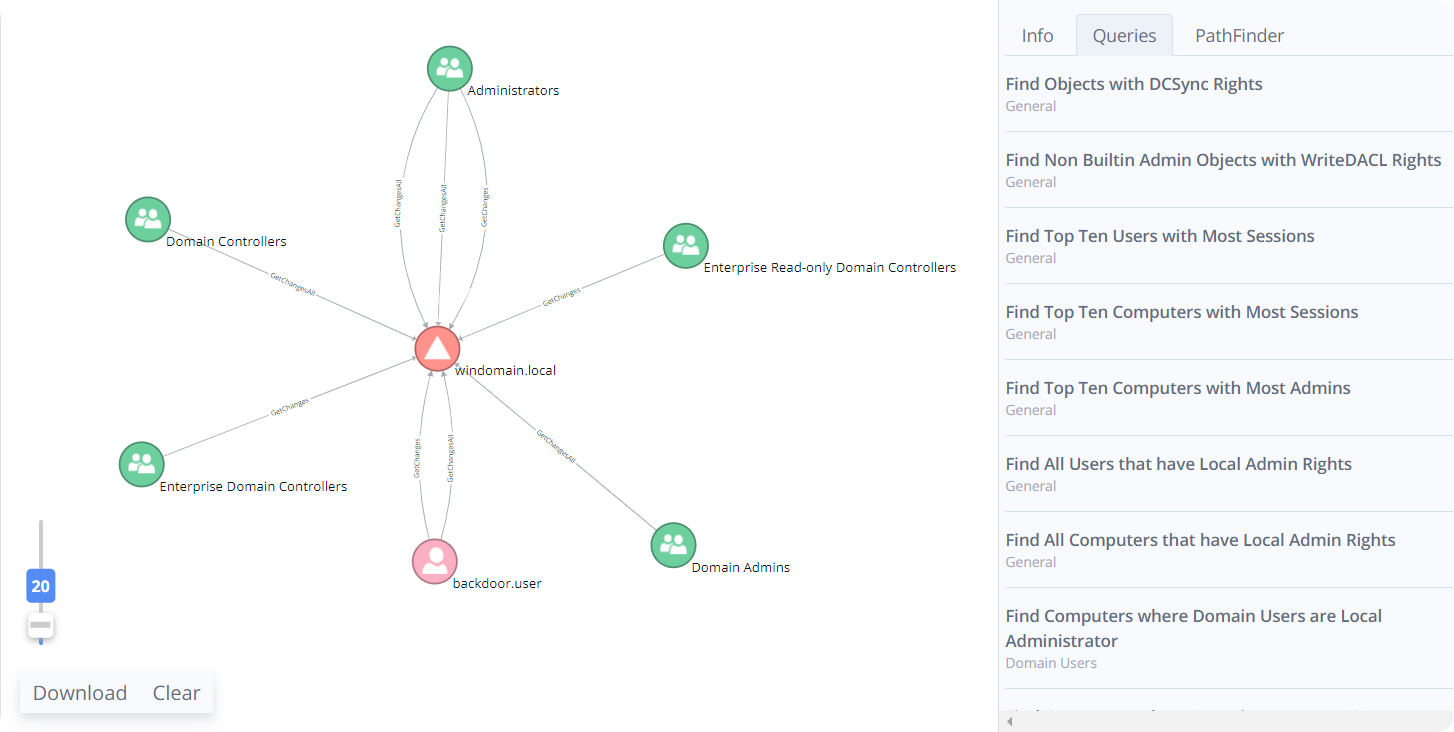
Active Directory Mapping
Privilege Mapping & Visualization
Vulnerability Assessment
Attack Path Detection
Actionable Remediations
Why Active Directory?
Active Directory is the key point to take over the network as a whole and discovering one weak spot is enough for compromising all connected assets at once. With the growth of the corporate, the domain environment becomes more complex because of merges and modifications. Thus, entities in the environment become more interdependent with each other.
Threat Centric Features
Advanced threat actors take advantage of Active Directory deficiencies most of the time. FSProtect, aims to restrict the adversary maneuverability by detecting vulnerabilities, misconfigurations, and hidden attack paths lurking in the complex relationships with minutes.
Active Directory Mapping
Privilege Mapping & Visualization
- Vulnerability Assessment
Attack Path Detection
- Actionable Remediations

Why Active Directory?
Active Directory is the key point to take over the network as a whole and discovering one weak spot is enough for compromising all connected assets at once. With the growth of the corporate, the domain environment becomes more complex because of merges and modifications. Thus, entities in the environment become more interdependent with each other.

Key Features
AD Inventory Enumeration
Localuser & Localgroup Enumeration
AD Vulnerability Assesment
Agentless Scanning
Detailed Vulnerability Documentation
Graph Visualization
Downloadable PDF Reports
API Interface